Given the continuous increase in registered vulnerabilities year-over-year and the risks posed by the availability of public exploits, vulnerability management remains a key component of an organization's security strategy. Installing new software and packages on endpoints may introduce new vulnerabilities, expanding the system's attack surface. Vulnerability management provides a structured approach to identifying and mitigating these security weaknesses.
Vulnerability management involves continuously assessing systems, applications, and networks to detect flaws within an organization's IT environment that threat actors could exploit. Organizations can reduce their risk of exploitation by regularly scanning for vulnerabilities, prioritizing them, and implementing timely remediation measures. A proactive approach to vulnerability management allows security analysts to detect and address vulnerabilities before they can be exploited. This strategy helps organizations reduce their attack surface, maintain regulatory compliance, and enhance their overall security posture.
The value of vulnerability management
- Proactive threat mitigation: By proactively identifying vulnerabilities, organizations can address weaknesses before threat actors exploit them.
- Improved security posture: Implementing a proper vulnerability management strategy enhances the organization's security and resilience against cyber threats.
- Regulatory compliance: Systematic vulnerability management helps organizations meet industry standards and regulations, building confidence among customers, partners, and stakeholders by demonstrating a commitment to security.
- Resource optimization: Vulnerability management involves assessing vulnerabilities based on their severity, potential impact, and exploitability. This risk-based approach ensures efficient resource allocation by prioritizing vulnerabilities according to risk assessment.
- Cost savings: Vulnerability management reduces the financial impact of data breaches and security incidents through proactive measures.
Wazuh for vulnerability management
Wazuh offers users a means to manage vulnerabilities within an IT infrastructure. It is a free and open source enterprise security platform that protects against security threats in cloud, on-premises, virtualized, and containerized environments. It provides a centralized view for monitoring, detecting, and alerting security events occurring on monitored endpoints.
The Wazuh Vulnerability Detection module helps users discover vulnerabilities in the operating system and applications installed on their monitored endpoints. The Wazuh agent collects a list of installed applications from monitored endpoints and sends it to the Wazuh server to detect vulnerabilities. The Vulnerability Detection module then correlates this software inventory data with vulnerability information obtained from the Wazuh Cyber Threat Intelligence (CTI) platform. Wazuh also offers a Security Configuration Assessment (SCA) module, which discovers misconfigurations that malicious actors can exploit to gain unauthorized access to systems and data.
The Wazuh Vulnerability Detection and SCA modules allow security teams to detect and remediate vulnerabilities promptly, strengthening organizations' security posture.
Wazuh Cyber Threat Intelligence (CTI) platform
The Wazuh CTI platform aggregates vulnerability data from diverse sources, such as operating system vendors and vulnerability databases, consolidating it into a unified and reliable repository. A core component of the CTI platform is the Vulnerability Detector Provider (VDP), which organizes all vulnerability information from different vendors into a single, reliable source. This variety of sources ensures that the Vulnerability Detection module covers various operating systems and applications. The module supports Windows, CentOS, Red Hat Enterprise Linux, Ubuntu, Debian, Amazon Linux, Arch Linux, SUSE, and macOS.
The VDP fetches vulnerability data from multiple sources, normalizes it into a standard format (CVEv5), and augments it to create the CVEv5 vendors' vulnerability content. This content is merged with intelligence data generated by the Wazuh threat intelligence team, which includes operating system base rules and product translations. The final result is a unique document for each CVE. The document is published through the CTI API, allowing the Wazuh manager to download and update its vulnerability information.

Wazuh Security Configuration Assessment (SCA) module
Wazuh SCA provides insight into your security posture by performing configuration baseline checks on services and applications running on monitored endpoints. Wazuh uses known regulatory standards such as CIS benchmarks, NIST, GDPR, and HIPAA to assess the security configurations of IT assets. These regulatory standards provide a global benchmark for best practices to help organizations enhance their IT hygiene. For example, the CIS benchmark offers guidelines for best security configuration practices and recommends various vendor products.
Wazuh out-of-the-box SCA policies are written in YAML and are primarily based on the CIS benchmarks. Wazuh also allows users to use custom or extend existing SCA policies to fit their requirements. The Wazuh agent maintains its local database, which stores the current state of each SCA check and reports the differences detected between scans to the Wazuh server. SCA scan results appear as alerts with detailed information whenever a particular check changes its status between scans.
Tackling vulnerability management challenges with Wazuh
Comprehensive vulnerabilities insight
Some organizations lack visibility of their assets and associated vulnerabilities, making it difficult to address vulnerabilities strategically. Wazuh provides a clear view of vulnerabilities identified in all monitored endpoints, allowing you to analyze and remediate them.
The Wazuh vulnerability dashboard provides users with the severity of detected vulnerabilities at a glance. It also highlights the vulnerabilities with the highest count and the most impacted endpoint, operating system, and packages.
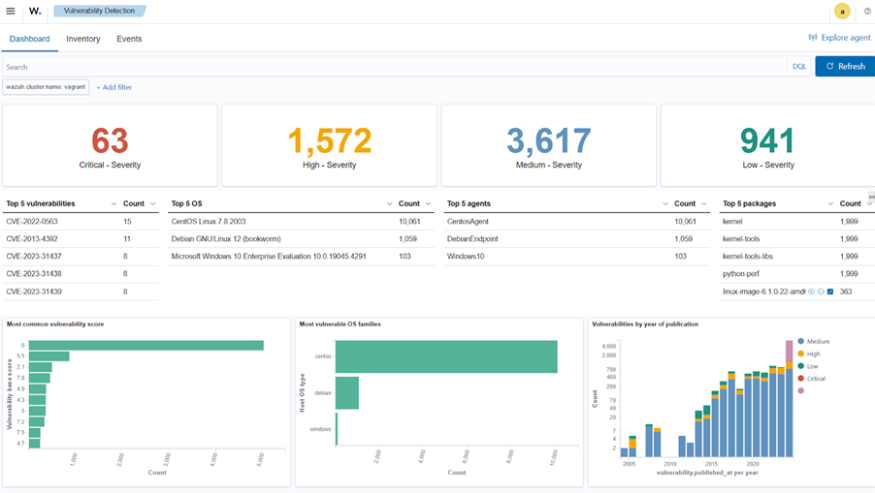
Prioritization of vulnerabilities
Prioritization helps organizations allocate resources to remediate vulnerabilities. Wazuh uses the Common Vulnerability Scoring System version 3 (CVSS v3) to group discovered vulnerabilities by severity. It also highlights the most impacted endpoints, operating systems, and packages.
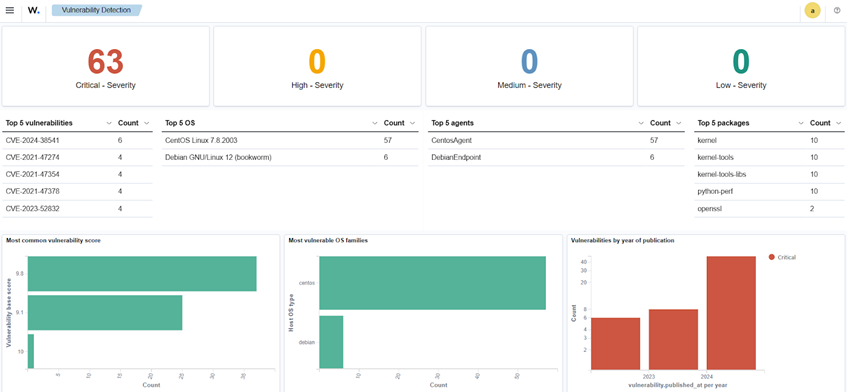
The vulnerability alerts on the Wazuh dashboard provide details and include recommendations for remediating identified vulnerabilities. Users can leverage this information to prioritize and create remediation plans by identifying critical vulnerabilities, the affected applications, and assets. The image below highlights the critical vulnerabilities identified by Wazuh. The dashboard shows the vulnerability base score, affected endpoints, vulnerable packages, and the number of occurrences of each vulnerability (CVE).
Monitoring and reporting
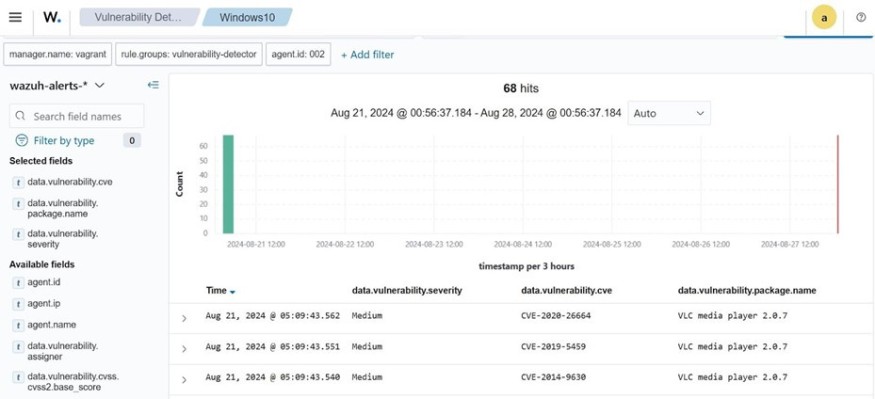
Organizations may need more information to manage vulnerability due to the volume of vulnerabilities and the pace at which new ones are detected. Wazuh allows users to monitor and track the vulnerabilities discovered on the monitored assets. Alerts are generated on the Wazuh dashboard when vulnerable software or packages are discovered on a monitored endpoint. Once a vulnerability is remediated, either by updating or removing the vulnerable package, an alert will appear on the Wazuh dashboard to notify you that the vulnerability has been resolved. Wazuh also enables users to generate vulnerability reports from the dashboard, which help demonstrate to stakeholders the organization's efforts to enhance its security posture. The image below shows the alerts generated on the Wazuh dashboard when a vulnerable VLC media player is detected on a Windows endpoint.
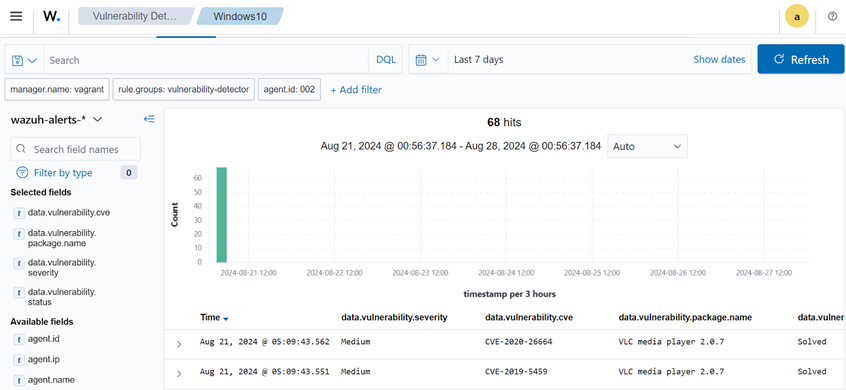
Additionally, an alert is triggered when the VLC media player package is uninstalled from the endpoint. The image below illustrates the vulnerability status following removing the VLC media player package.
Ensuring compliance with regulatory standards
Ensuring compliance with regulatory standards strengthens an organization's IT infrastructure security posture. However, some organizations may struggle to assess compliance due to the infrastructure's diverse applications, databases, and third-party components. With Wazuh SCA capability, organizations can assess the security configuration of various technologies against standards like the CIS Benchmark.
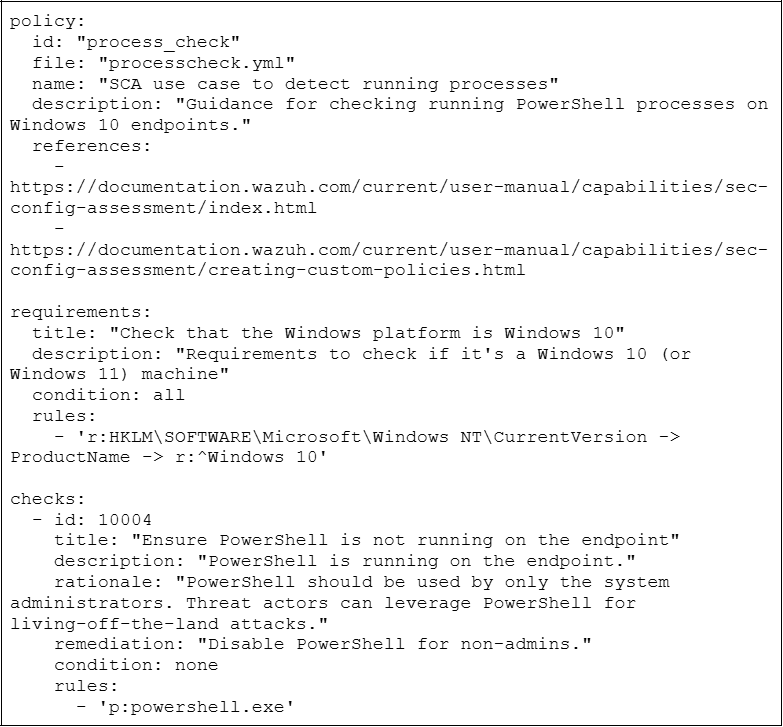
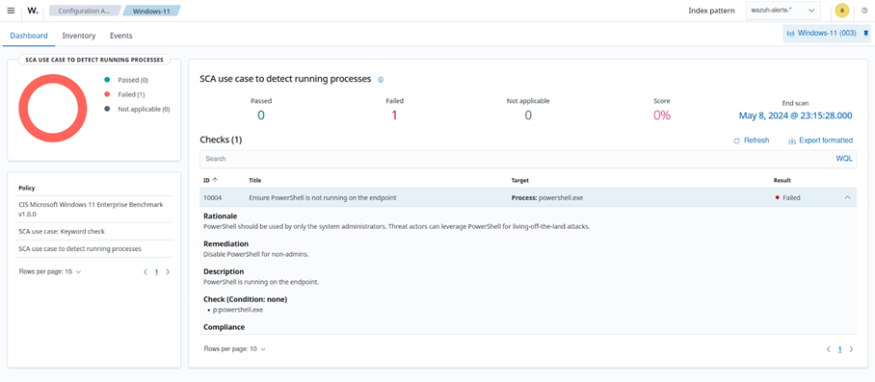
Users can leverage custom SCA policies to detect misconfigurations and system flaws specific to their environment. This includes issues such as passwords in configuration files and the presence of software or running processes that could be taken advantage of by a threat actor. This section of the Wazuh documentation demonstrates using a custom SCA policy to detect PowerShell access by a standard user. This flaw creates a security risk as threat actors might exploit this access and compromise the system using attack techniques such as living-off-the-land (LOTL). A custom SCA policy named processcheck.yml was created to scan a Windows endpoint for processes named powershell.exe.
The image below shows the result of the custom SCA policy and a description of the check, its rationale, and how to remediate the identified flaw.
Conclusion
As an organization's assets increase, its attack surface expands, making it vulnerable to various attack vectors. Vulnerability management ensures that assets are properly secured by addressing identified flaws. Wazuh XDR and SIEM provide users with tools to detect vulnerabilities and support the vulnerability management lifecycle through their vulnerability detection and SCA capabilities.
Learn about Wazuh by exploring the documentation and joining the user community.
© 2025 ScienceTimes.com All rights reserved. Do not reproduce without permission. The window to the world of Science Times.












